The
banking trojan Dridex (also known as Cridex, Feodo, Geodo, etc.) has
been distributed in the past via malicious documents containing macros
sent by E-Mail. Just yesterday we discovered a new distribution method
that is undetected by the various Sandbox solutions we have access to
and all AV engines. We were able to happily share and send those
infected files via Skype, Gmail and other platforms. So while Dridex
itself isn't new, the distribution method definitely is --- and it will
be very successful looking at current 0% detection ratio. In a sense, it
is a "zero-day-distribution" method so we decided to use that term. ;-)
In
this blogpost we will analyze a sample file, demonstrate the
distribution method and cover some context, finishing up with a link to
the updated VxStream Sandbox report at hybrid-analysis.com, as our
engine is able to detect and execute the dropper code as of now.
At
Payload Security malware analysis and working together with the
IT-Security community is our passion, which is why we try to be as
reactive and response as possible to new evasion techniques. As a
reminder of latest additions to VxStream Sandbox, here are a few
pointers:
- Bypassing "image click" macros
- embedded .[diag]cab Office attack vectors
- Cerber using DOT files with password prompt
... but let's get down to the nitty gritty of this Dridex campaign.
In this example, we will be
taking a look at "remittance advice 58.docx" (SHA256:
da82eaeba71eeb95d643b0343b2c095d72b686314cd340631aa8d9fe08a74714).Initial Manual Assessment
As
has been a recent trend we see for targetted attacks (more on that
later), this malicious Office file does not contain any macros (or
exploits, actually) to execute the payload:
Instead,
the document contains an embedded file, which can be extracted from the
"oleObject1.bin" file in the "embeddings" folder. In this case, as it
is a Word file, the relative pathway would be word/embeddings/oleObject1.bin. Let's take a look:
As a quick initial assessment of the file, let's take a look at some of the strings we can find:
We quickly detect the following key information:
- a "Windows Shortcut" (.LNK) file seems to be embedded
- a reference to the Windows command prompt
Taking a deeper look we quickly see the actual "dropper" code, which is a powershell command:
A more readable format:
What it does:
- requests a PHP file from a remote server
- downloads the PHP file (which is actually a PE file) and renames it to "calc.exe" (probably in hope of being a bit less suspicious)
- executes the downloaded file
The downloaded file is Dridex.
Using Windows Shortcut (.LNK) files as an "under-the-radar"
distribution method is actually not that new for the group behind
Dridex, as they have used that exact method as part of an E-Mail
attachment. So in a sense this is just a new variation, albeit it is
quite nested and obviously successful looking at the detection rates.
If you wanted to confirm that the file is Dridex, you could e.g. check the ET PRO rules, which are integrated into all VxStream Sandbox reports, if you have the appropriate license:
If you wanted to confirm that the file is Dridex, you could e.g. check the ET PRO rules, which are integrated into all VxStream Sandbox reports, if you have the appropriate license:
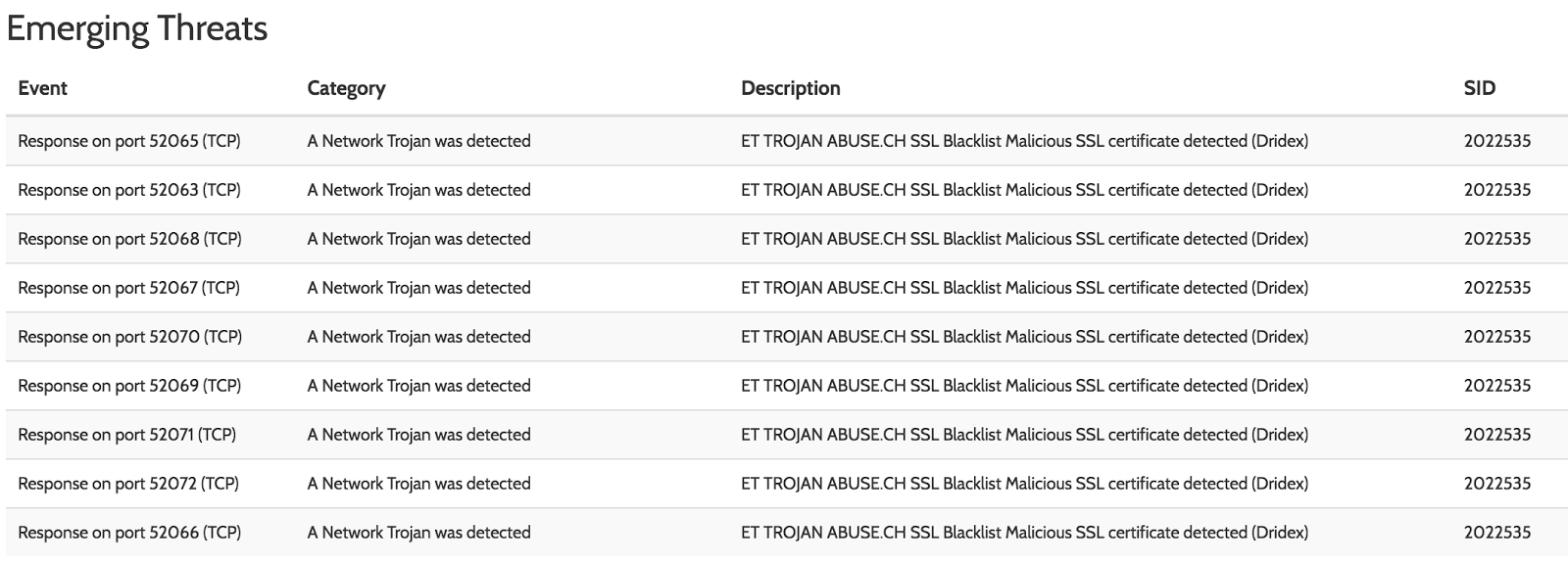 |
| Dridex identified by ET PRO Rules |
A normal execution of Dridex will download an encrypted DLL and after some security checks, the configuration file.
Why "Common" Dynamic Analysis Fails
Simply
opening the document will cause nothing to happen initially. Instead,
the embedded file has to be double-clicked. This is the first "hurdle"
that most Sandbox systems will have difficulties with.
After double-clicking the file - on a default configured system - an additional prompt will have to be passed:
...
only if we click "Open" on that prompt, the actual LNK file and
consequently the Command Prompt -> Powershell execution chain will
trigger and download Dridex.
Why is it a targetted attack?
The
server(s) hosting Dridex seem to be denying access based on the
geolocation. This can either be a temporary countermeasure while testing
sandbox detection ratios or it can be a hint at a targetted attack for a
specific region. We were only able to download the sample if the source
IP was located in the region highlighted in green:
All other countries were denied downloading the sample in our case.
How does VxStream Sandbox perform?
Obviously,
we wouldn't be writing this blogpost if VxStream Sandbox would be
performing poorly. ;-) To be fair, as we discovered the first files just
yesterday, our engine was not parsing the embedded .LNK file properly,
as we had been focusing on embedded executables, Powershell, VBScript,
Javascript and some other file types. Nevertheless, as the sandbox has
technology included that can deal with these kind of attacks in
principle, it was an easy task to add support for the new missing file
type. After updating the live systems (in less than 24h, noted), we
successfully flag the file as malicious *without* the help of any AV
detection. Here is a few example screenshots:
Link to report: https://www.hybrid-analysis.com/sample/da82eaeba71eeb95d643b0343b2c095d72b686314cd340631aa8d9fe08a74714?environmentId=100
Hunting more samples
This
was actually quite interesting. Based on the embedded file "absolute
pathway" that is included in the Word documents, were able to discover
additional files that reach back to May/June on our public webservice:
Final Words
In
this blogpost we demonstrates a brand new Dridex distribution method,
outlined some initial assessment and demonstrated how important "state
of the art" security solutions and vendor responsiveness is, as the
groups behind malware are very creative, especially considering the
money business that ransomware, banking trojans, etc. has become. Stay
safe and we hope you enjoyed the read.
Other SHA256s:
bc17109629c455e6bbcf25d313f3c79234a2facf7691bef3df26cc2537071809
96d43a519e857663a78eff84b56bbb0343c7c6fb4b5814c0fd7a302abc74bd79
06eab8037525ba0ac8dc62512a149aea3786c33cd6e7d08b9c5b175777c31da3
1382a68b7a9b0f20670162d8cd8dc91ad27c556ec166a351910cfffeda1f9353
da82eaeba71eeb95d643b0343b2c095d72b686314cd340631aa8d9fe08a74714
Other URLs:
meow://4thkantonind.top/egypt/hashish/afghankush.php
meow://47matroskin.top/nazareth/animals/listen.php
meow://17uhrtreuhand.top/nazareth/animals/listen.php
meow://37virginiaslim.top/nazareth/animals/listen.php
meow://17uhrtreuhand.top/nazareth/animals/listen.php
Follow us on Twitter: https://twitter.com/payloadsecurity
Public Webservice: https://www.hybrid-analysis.com/
VxStream Sandbox: https://www.payload-security.com/products/vxstream-sandbox












