While checking submissions on our webservice we discovered that someone uploaded a "new" version of Pafish (by a0rtega). Pafish is a demo tool that performs typical anti-VM tricks in use by common and sophisticated malware. The new version of Pafish adds a lot of new VM and system trace checks, especially for VirtualBox. As is known, VirtualBox happens to be the default analysis environment of most sandboxes (including Cuckoo Sandbox's Malwr service and our own Hybrid-Analysis.com's free malware analysis service).
To be honest, the new version of Pafish did detect our virtual machine environment using some of the new methods - and it is impossible to prevent all types of detections ahead of time. More importantly, it is necessary to stay on top of the game and offer a software product that is agile and can adapt quickly. That is one of the principles we try to live up to and thus we always try to improve quickly and update VxStream Sandbox when necessary. A benchmarking tool like Pafish is a perfect development tool, because it's a very straightforward, comparable and easy way to stay on par with typical anti-VM methods. On a side note: the "new" release of Pafish is actually not that new, it was released at the beginning of this year - i.e. it's about two months old. One would think that well established and well known sandbox systems like Malwr, ThreatTrack or Comodo would have adapted by now - but to our surprise this is not the case.
First of all, this is how it should look if you run Pafish v0.4 (current state of VxStream Sandbox):
The green "OK" indicates that the specific check was passed and Pafish was not able to detect that it is running on a virtual machine. Here is one full report of VxStream Sandbox on our webservice (we copied the different console outputs into one screenshot to save space).
This is how the instance of Cuckoo Sandbox running on Malwr performed:
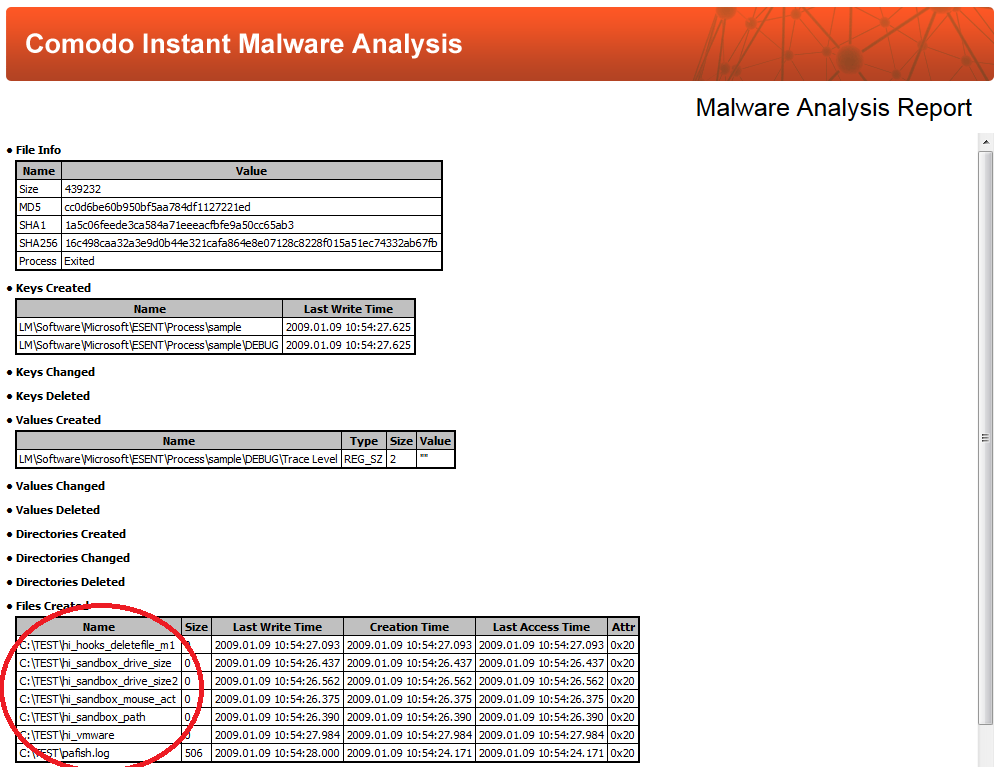
This is how Comodo Instant Malware Analysis performed:
The created "hi_" files indicate detection.
This is how ThreatExpert performed (it seems to be using VMWare as environment - and those checks are very old):
Sadly, Anubis failed to even parse the file, but to their defense the service is not being actively maintained it seems:
Finally, let me quote from ThreatTrack's main page before finishing up with this blogpost:
"Our solutions detect the world's most sophisticated malware – including
Advance Persistent Threats (APTs) and targeted attacks – and empower you
to completely eliminate those threats from your network."
I am assuming that "the world's most sophisticated malware" does not include simple VM checks *grin*. Nevertheless, I would like to underline that we are not claiming to include the "best anti-VM technology" possible (and that's a big difference to other malware analysis vendors), but at least we try to get the basic homework done. Big vendors that claim they include "high-end technology" should be doing the same (taking care of their homework) and spend less money on marketing bla-bla. Of course, it is a bit unfair to mention Cuckoo Sandbox with its malware service Malwr in this context, because it is based on an open-source tool, but I added it for completeness sakes, as it is the most popular free malware analysis service available.
Update (03/23/15): One of the Cuckoo Sandbox authors complained to us last week that they never claimed to have anti-vm technology included in their sandbox system, which might be true for the sandbox system itself, but this blogpost is focusing on public online services only (which is why we now updated the blogpost title, it might have been a bit inaccurate before), their output and not theoretical capabilities of the tools behind the services. The assumption that an online service demonstrates the latest and greatest version and capabilities of a sandbox system is valid one in our eyes, because a user probably expects an online service to try to analyze malware as good as possible, at least when it is about important aspects of malware analysis.
Update (03/23/15): One of the Cuckoo Sandbox authors complained to us last week that they never claimed to have anti-vm technology included in their sandbox system, which might be true for the sandbox system itself, but this blogpost is focusing on public online services only (which is why we now updated the blogpost title, it might have been a bit inaccurate before), their output and not theoretical capabilities of the tools behind the services. The assumption that an online service demonstrates the latest and greatest version and capabilities of a sandbox system is valid one in our eyes, because a user probably expects an online service to try to analyze malware as good as possible, at least when it is about important aspects of malware analysis.